The boundary between cyberspace and real life is gradually blurred. With the development of the Internet of Things, individuals and various types of devices are increasingly connected to the network, and various items are seamlessly integrated into the information network system. Machines and robots can sense and analyze data to enable real-time remote control. The Internet of Things will change the way people live, work and even communicate. In the long run, no company can avoid its influence. However, the huge opportunities bring new challenges, especially in terms of security.
Security is at the heart of the Internet of Things, especially in terms of identity. If people need to connect their homes, cars and factories to the network, they must be safe. Individuals, machines, and devices must be securely authenticated and only authorized to access them. Users' private data and corporate secrets must be protected from theft and fraud. At the same time, IoT security design must also be easy to use without sacrificing any user experience. Therefore, security needs to be designed from the beginning to the IoT system, rather than being added later.
The importance of security hardware to the Internet of Things
Stuxnet, BlackEnergy, and a series of other recent attacks have proven that relying on software alone cannot effectively protect IoT systems. Blackmail hackers can often bypass security software and remotely control the system. Combining software with hardware provides the best balance between security and flexibility. Even if the security software does not work, the security chip can still provide protection.
User identity in the Internet of Things
IoT users require remote access to information on their devices, but this also requires a high degree of ease of use and security. User name and password verification often fail to meet these requirements because people often think that password entry is cumbersome and easy to steal. Recently, the FIDO (Fast Network Authentication) Alliance has released an open, extensible, interoperable multi-factor authentication mechanism standard.
IoT users can get two benefits from FIDO. First, their security has improved. Second, the complexity of device verification management has been greatly reduced. As shown in Figure 1, FIDO allows users to obtain their network account through a local hardware security verification code, which they can use to verify other systems, whether or not they have a PIN.
Device identity in the Internet of Things
With the rise of the Internet of Things, device security, especially device identity, is becoming more and more important. IoT devices control critical systems such as cars, factory systems, door locks, and security cameras. At the same time, they are also threatened by many networks. To block unprivileged participants and provide security, IoT devices must be able to authenticate in both directions with users, other devices, and the cloud. Fortunately, device identity technologies (such as IEEE 802.1AR) are very mature and widely used.
Password authentication is the best way to authenticate IoT devices. IoT devices can be built, maintained, and used with long keys. Therefore, there is no need to use a password for device authentication at all. Security hardware protects these keys from theft.
Some security chips—for example, the Trusted Platform Module (TPM), which is an open standard—not only establish device identities, but also design encryption and device detection. The integrity of the monitoring system is especially important for the Internet of Things, because illegal devices that obtain certain certifications can cause real physical damage.
Identity in the Industrial Internet
Industrial Internet refers to the application of the concept and technology of the Internet of Things in industry. For example, a new generation of manufacturing uses a network to integrate the entire supply chain from supplier to consumer, enabling suppliers to tailor production to market needs. In such an environment, authentication must be performed and end-to-end communication protected to ensure the security of all information, including consumers and suppliers.
To ensure the safety and integrity of the system, the safety controller can be integrated into all parts of the industrial Internet system, tracking everything from product reservations to production lines to transportation, distribution, wholesale and retail through devices such as customers' tablets. These security chips establish products, devices, and user identities for encryption and authorization while maintaining device uniformity. In addition, these security solutions provide protection for sensitive IP and process technologies.
in conclusion
In the Industrial Internet, reliable identity authentication for users and devices is essential. Without a reliable identity, an attacker can cross the boundaries of the network and reality. Such an attack is currently taking place. With the application of many IoT technologies, the impact of these attacks is not limited to smart homes or connected cars, but also extends to industrial automation, healthcare and other fields.
Fortunately, standards and technologies for reliable authentication are now available without compromising the user experience. Hardware security must be used to limit the impact of shortcomings that software cannot eradicate. Reliable identities and secure hardware are a must-have in designing IoT systems and other systems that connect cyberspace to the real world, and that's the only way to be secure.
Figure 1: Reliable authentication in FIDO (picture from FIDO Alliance)
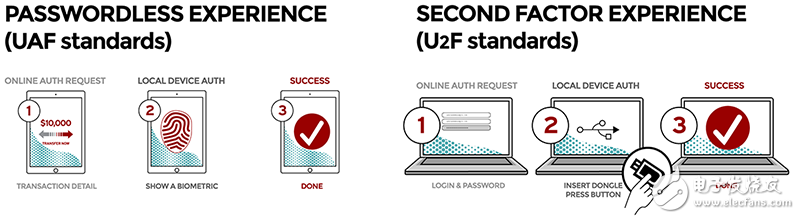
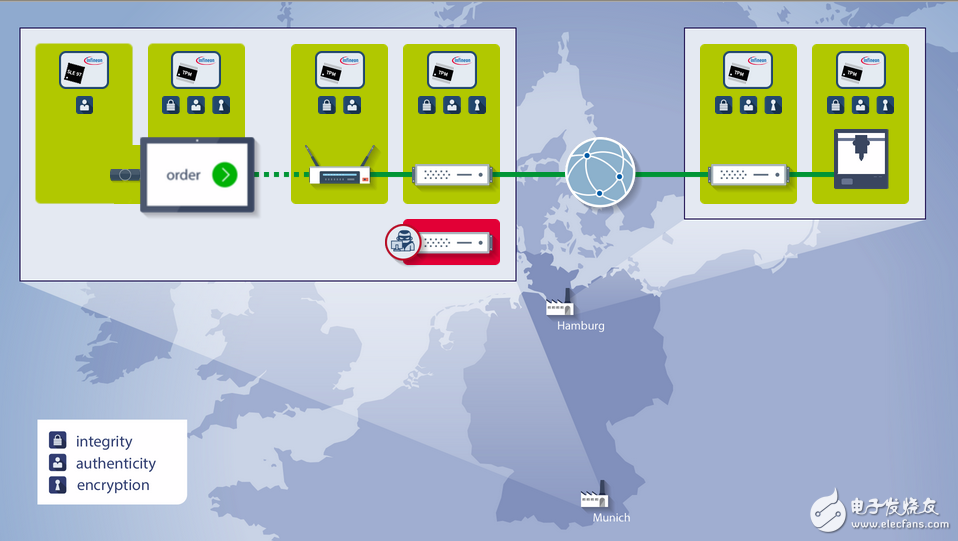
Figure 2: End-to-end security in the Industrial Internet
-------------------------------------------------- --------
This article is selected from the "Intelligent Hardware Special Issue" in April. More technical hot texts can be downloaded from the special issue page !

Key Switches
Yeswitch Electronics Co,.Ltd., found in 1995 in Taiwan, is specializing in manufacturing and supplying all kinds of switches, including Key Switches, Metal Switches, Toggle Switches, Rocker Switches, Automotive Switches,etc. Yeswitch Key switches, including Electrical Key Switch, CAM Lock , and self-lock key switch. It is made of Zinc alloy,stainless, brass, silver and other materials. Our key switches have three installation size, respectively are 12MM, 16MM and 19MM. It could used in wide range of applications, for example, ATM, POS machine, Computer host,recreation facilities, Cash register, elevator, electric cars,file cabinets, etc.
It is normally made of stainless,zinc alloy,brass and other metal materials, which is imported form Australian, so our products could enjoy the sound reputation in switch field with he high-end market strategy. Meanwhile, we are very familiar with UL, ROHS,SGS and related other authoritative approve standard in the switch industry.
We are focus on producing high standard and high quality switches, so our key switch is of high standard products , it could not only anti-explosion but also Anti-vibration. And we are also adhere to the three principles to serve our customers around the globe,namely,meeting global standard, accurate operation and on time delivery.
Key Switches
Key Switches,Momentary Key Switch,Key Switch 3 Position,Key Switch On Off
YESWITCH ELECTRONICS CO., LTD. , https://www.yeswitches.com